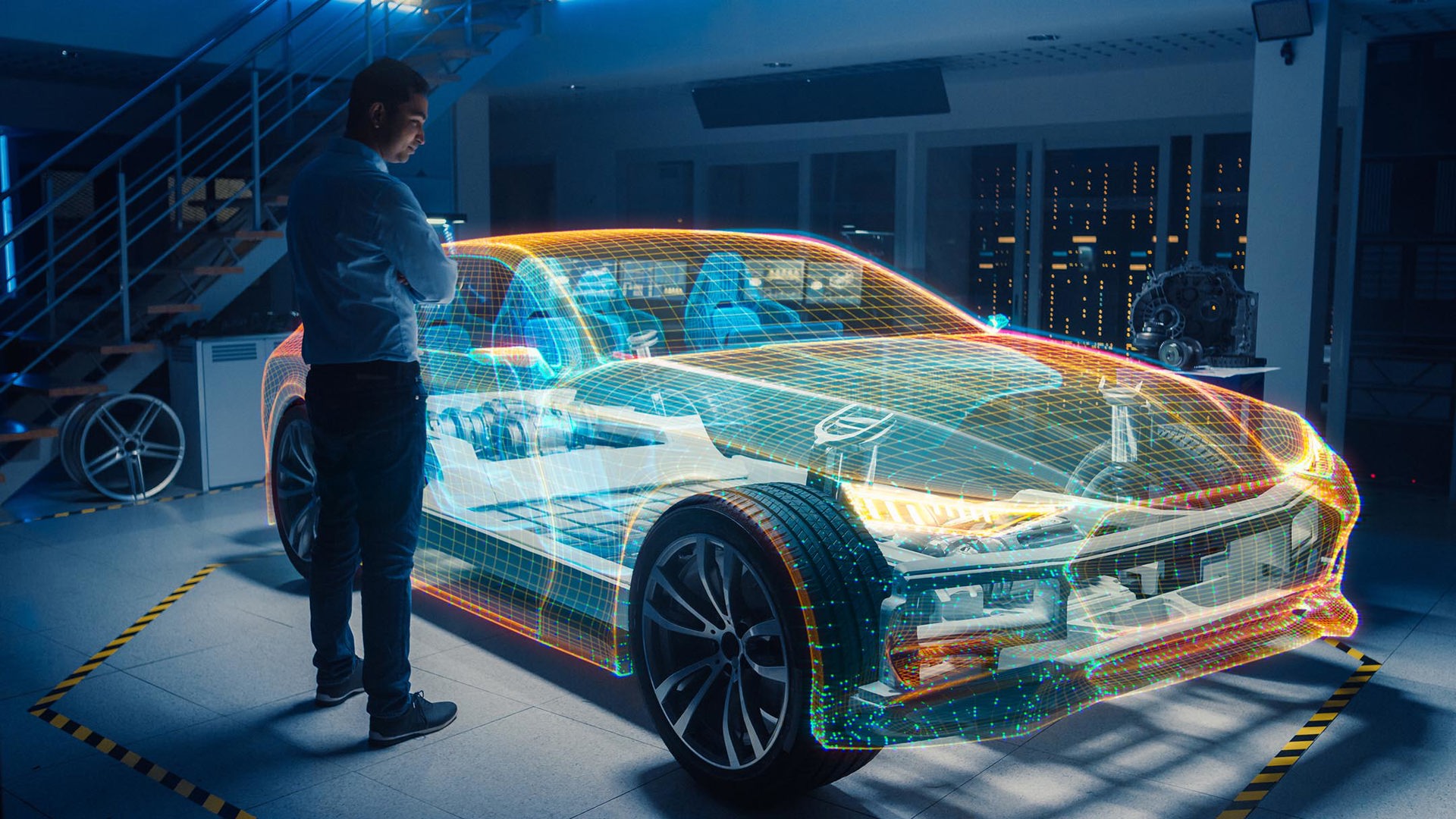
We don’t often think of our cars as cybersecurity risks until we step back and realize that modern vehicles are computers on wheels. Moreover, those computers are connected to the digital world through our data plans, phones, onboard apps, and other technologies, leaving us exposed to potential hackers and cybercriminals.
“Manufacturers want to collect a lot of information from these cars,” explains Robert Falzon, Head of Engineering at Check Point in Canada. “They’re also adding connected services, which means a vehicle will have an app associated with it, where the owner can control certain aspects of their vehicle’s account.”
Some of these connected features might be the ability to remote start the car or check fuel or charge levels via an app, emergency services like roadside assistance, Alexa or Google Home integration, artificial intelligence tools, and more.
Our vehicles are constantly communicating with the outside world, sometimes in real-time, and this interchange of data takes place more often than we might realize. Falzon offers the example of a vehicle equipped with OnStar, General Motors’ telematics and roadside assistance feature.
“That OnStar system has access to control sensors within the vehicle in order to determine if you have been in an accident,” he explains. “So information is being communicated externally, and the security and the data integrity of that communication is what we question.”
Another example, he adds, is a Tesla driver who could use the interface inside their vehicle to tell Tesla that they would like to purchase the self-driving feature. While purchasing a feature through an interface inside a vehicle is convenient, it also exposes the vehicle owner to a potential cybersecurity risk.
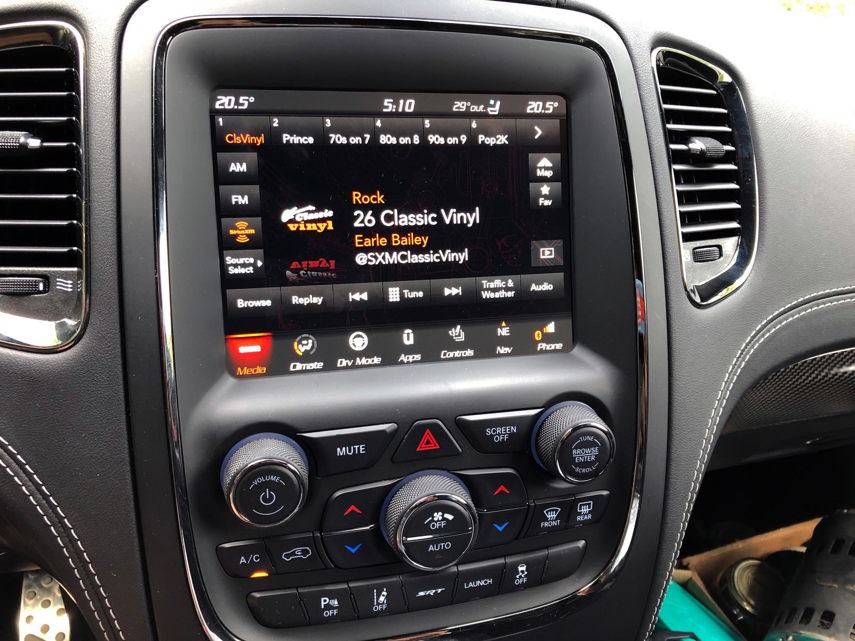
Exploiting Weaknesses
Cybercriminals can access a vehicle’s computer systems in the most unexpected ways. Speaking at a cybersecurity webinar, Yaniv Maimon, VP of Cyber Services at Upstream Security, explained how hackers in one particular instance were able to exploit a weakness in the infotainment system.
“They were able to control vehicles from multiple brands,” Maimon said. “In this case, they didn’t even need to hack directly into the vehicle. Instead, they got in through the SiriusXM app.”
Maimon explained that all the hackers needed was the vehicle identification number (VIN), and once they gained access to the vehicle via the satellite radio app, “they were able to lock and unlock the doors, start the engine, as well as view the location of the vehicle.”
In a worst-case scenario, Check Point’s Falzon adds criminals can steal personal data or even cause a collision. “In some cases,” he explains, “with some of the more connected vehicles, hackers demonstrated that they could cause the vehicle to accelerate. They can also hack into your phone if it’s connected to the vehicle.”
Security Shortcuts
One of the reasons we’re seeing these types of vulnerabilities is that vehicle manufacturers are eager to roll out new technologies as quickly as possible, Falzon explains. Sometimes, they’re so eager to bring a new technology to market that the security measures they put in place aren’t as comprehensive as they should be.
Fortunately, it’s not all bad news, and although cybersecurity experts are bringing these risks to our attention, they stress that we shouldn’t panic or be afraid to drive our vehicles. These types of cyberattacks are still few and far between.
Both vehicle manufacturers and vehicle owners still need to do their part to limit the risk, however. “The more we talk about cybersecurity incidents, and the more people hear about these things, the more pressure there will be on [vehicle manufacturers] to improve security,” Falzon says.
Vehicle manufacturers can and should improve security, but according to Falzon, they’re not always as proactive as they could be. “There’s a lot they can do,” he says. “The challenge is that doing those things costs money.”

Protect Yourself
While manufacturers need to step up to the plate and prioritize security, when they do so, it’s vital that we, as consumers, follow through and take advantage of the tools they give us.
Falzon offers the example of a Tesla owner who got hacked. “Tesla had offered him the ability to turn on multi-factor authentication on his app,” he explains, “but he chose not to. Because of that, he made himself more susceptible to an attack.”
Moreover, if the manufacturer of your vehicle notifies you that your vehicle needs a firmware update (whether over-the-air or at a dealership), you’ll want to get it installed as soon as possible because these often include software patches to bolster security.
Electric Vehicles
While most modern vehicles are potential targets for hackers, Falzon says that electric vehicles can be especially susceptible, which is why he recommends common-sense measures that all EV owners should consider.
“If you drive an electric vehicle, and you’re at a charging station, don’t connect your vehicle to the public Wi-Fi because your vehicle doesn’t have the same protections that consumer devices [like your smartphone] do,” he explains.
Furthermore, Falzon recommends caution whenever charging an EV at a public station. “Many of these charging stations use older versions of, for example, the Android platform. Android has vulnerabilities in those older versions, and those vulnerabilities are being actively exploited,” he says.
If you plug your vehicle into a charger that has been compromised in some way, that charger may steal information from you. “That includes things like billing information, the condition of the vehicle, or how the vehicle should respond to the energy coming into it,” Falzon adds. “So a hacker could theoretically cause your vehicle to overheat or overcharge and cause damage.”

His advice is to stay away from any chargers that look like they might have been tampered with. “Also, don’t use chargers that are from a vendor that you’re not familiar with,” Falzon adds. “As an electric vehicle owner, you get to know which vendors are well established. Stick with those, because their equipment is regularly updated and better managed.”
Whether you drive an EV or not, the bottom line is that we all need to be more vigilant. “We all need an increased awareness about what it is we’re getting into when we buy a new vehicle today, and what information we’re sharing,” Falzon concludes. “Don’t make yourself an easy target. Use multi-factor authentication, update your vehicle, take basic security measures, and change your passwords on a regular basis. This kind of general cyber hygiene will help keep you safe.”